Infiltrate
Metasploitable
In this post I am going to be diving into some web application hacking and some techniques used for recon and infiltrating a website. First, I want to start off by explaining a little bit about Metasploitable. This is an intentionally vulnerable machine that pretends it is a webserver, the goal of using this VM is to practicing learn how to use different tools and techniques to exploit it. Please do not expose this to the internet. Once, you log in and gather the IP of the MS server you can switch to your Kali machine and start hacking away!
This is for educational purposes only, do not attempt this on any thing you do not own or have permission on!
Now for the fun stuff, here we are at the login page for the DVWA(Damn Vulnerable Web App), now at the bottom of the page it tells you clearly what the login and password is, but that’s no fun!
First, let’s run a nmap scan on the IP, in this example I am using -A which is a highly aggressive scan and will most certainly make a TON of noise on a network. If you are looking for stealth you can use the -sS option it will be slower but make a lot less noise. If you’re not familiar with nmap and what it can do I suggest reading the man pages!
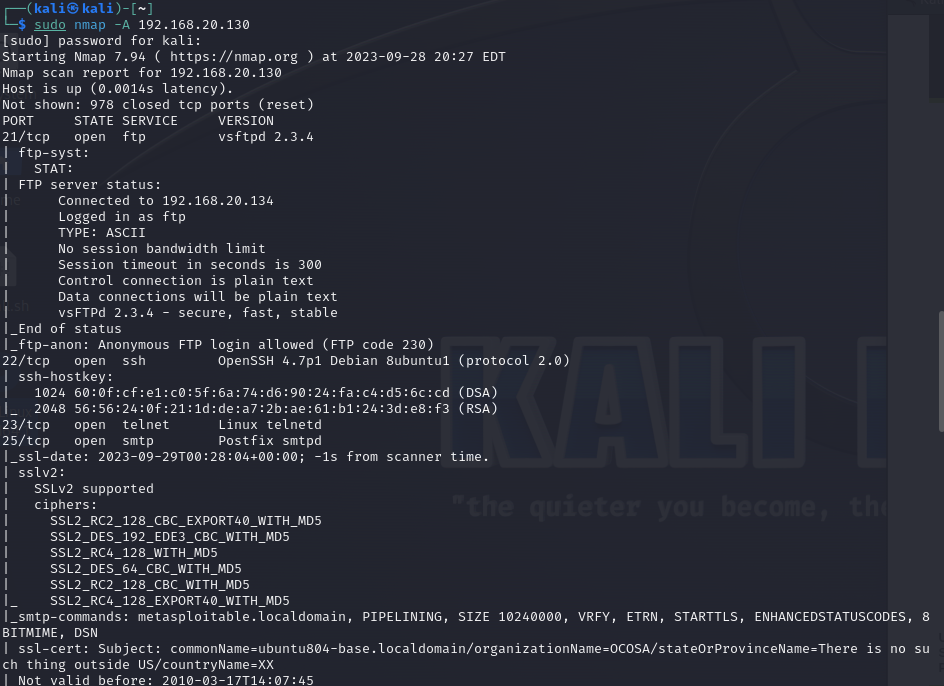
There is a LOT of information here and a lot more I can not fit in the screenshot. Here’s why all this is useful, I can tell the OS and versions they are using (a quick google search with unveil a plethora of vulnerabilities I can use), network topology, and nmap can allow you to run script scans which can unveil misconfigurations (or even worse default configs) in the system to be exploited! Now let’s try to login to the app.
I like to check out the robots.txt page, if you’re not familiar with what the robots.txt on web pages click here to learn more about it https://www.cloudflare.com/learning/bots/what-is-robots-txt/
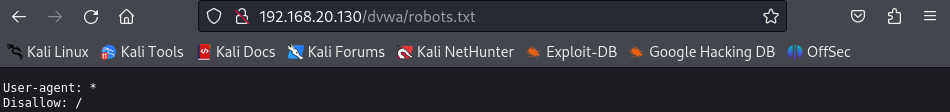
Ok bummer nothing is here, lets break out dirb. dirb is going to scan a URL and find any directories on a URL either using its default wordlist or you can supply a custom wordlist. It will enumerate all the directories and give you a list of response codes from the website.
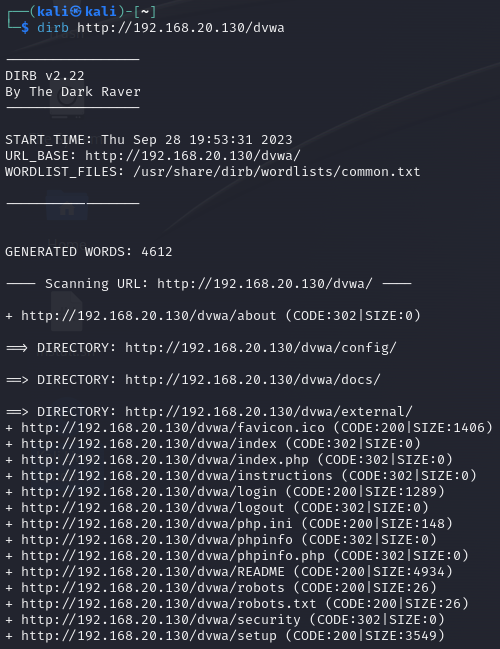
Now we have something to work with, we have hits on the favicon.ico, login, php.ini, README, robots, robots.txt, and setup pages. I am going to take a look at the README page first and see what I find.
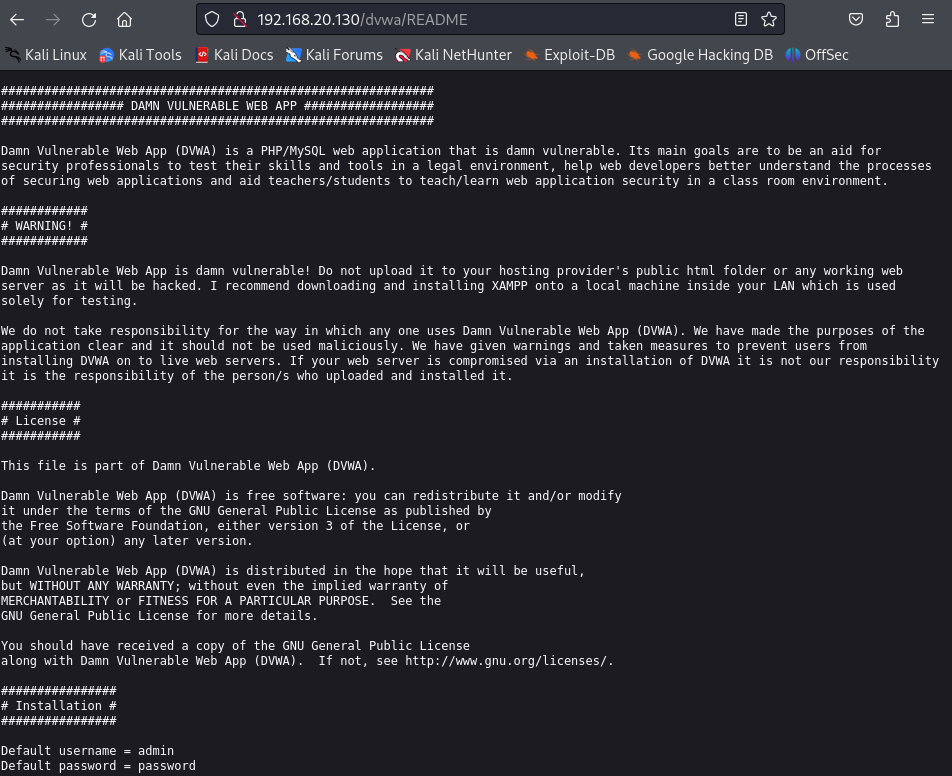
Bingo, I got a username and password at the bottom ( of course this is a basic installation and warning guide, but you would be surprised the number of websites out there leaving sensitive information out there unknowingly). Let’s login.
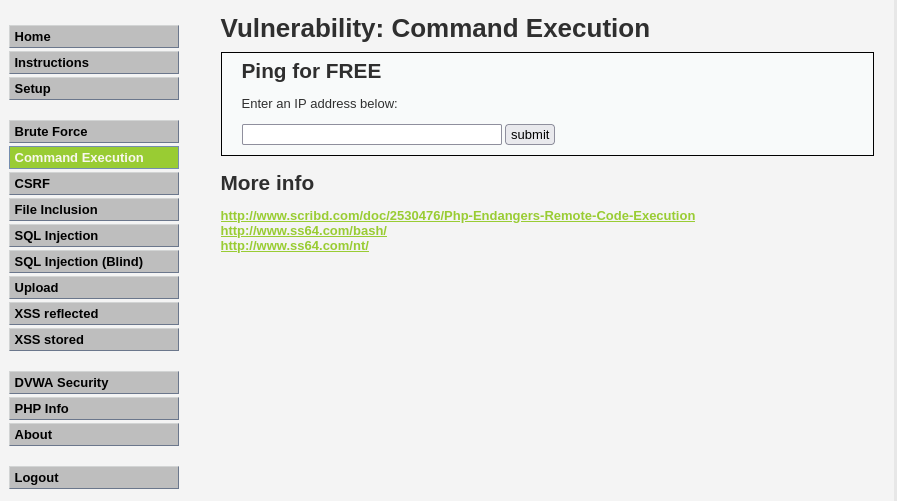
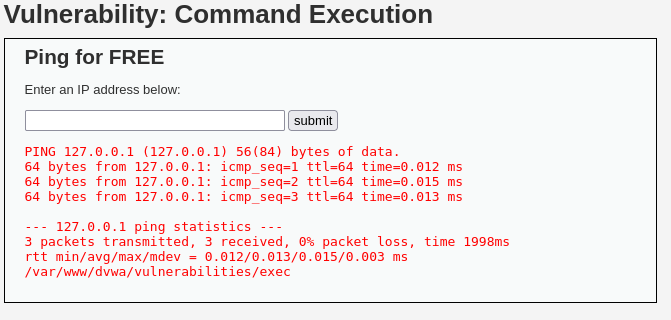
Now that we are in you can practice different attacks and techniques, let’s try to execute some commands and see what happens.
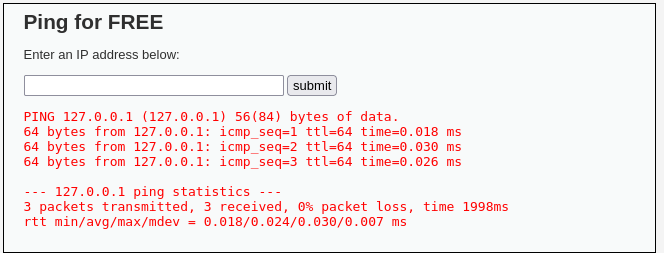
I input ‘127.0.0.1’ and got this response. I wonder what would happen if I tied this together with some basic commands, let’s see if the developers are doing proper input validation.
I input ‘127.0.0.1; pwd’ and look what happened we got it to print the working directory for us!
This is just a very basic overview of getting into web application hacking, there are 3 security levels on DVWA (high, medium, low) and you can view the source code for each page to get a sense of how it gets hardened at every level. I encourage you to play around with different tools and techniques for breaking the system.